- Forums
- :
- Core Technology - Magento 1.x
- :
- Magento 1.x Technical Issues
- :
- Re: Ransom Ware on Clean install of 1.9.2.4
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
Ransom Ware on Clean install of 1.9.2.4
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ransom Ware on Clean install of 1.9.2.4
I have a clean install of 1.9.2.4 on a beta site.
Is not spidered by Google or anyone else.
It's only about 2 weeks old. I am using and editing the built rwd in theme.
I installed the Smart Slider 3 extension (which I have been using for a while).
Site was working fine for 2 weeks after that.
Then I Installed the Helios Vimeo Video Gallery extension at about 3.25pm.
At 6.30pm that same day all my files were encrypted and a file with the README_FOR_UNLOCK.txt in all the folders.
Inside it reads...
###
ALL YOUR WEBSERVER FILES HAS BEEN LOCKED
You must send me 1 BTC to unlock all your files.
Pay to This BTC Address: 1859TUJQ4QkdCTexMTUQYu52YEJC49uLV4
Contact tuyuljahat@hotmail.com after you send me a BTC. Just inform me your website url and your Bitcoin Address.
I will check my Bitcoin if you realy send me a BTC I will give you the decryption package to unlock all your files.
Hope you enjoy ![]()
###
Also the menu item for the Vimeo Gallery was now gone.
So it seems pretty obvious that it is the Helios Vimeo Video Gallery but how can I tell ? I am really concerned that the new version of Magento allows this to happen, I thought it was patched for this long ago ?
My site permissions are all good. I am running ConfigServer Firewall. My passwords are strong. It passes all tests on magereport.com
Thoughts ??
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Ransom Ware on Clean install of 1.9.2.4
Hi @mousepad
It is a obvious ransom ware attack on you site. I think by Beta site you means to say it was under development.
Just by applying the patch or using latest version of Magento your site does not become 100% secure.
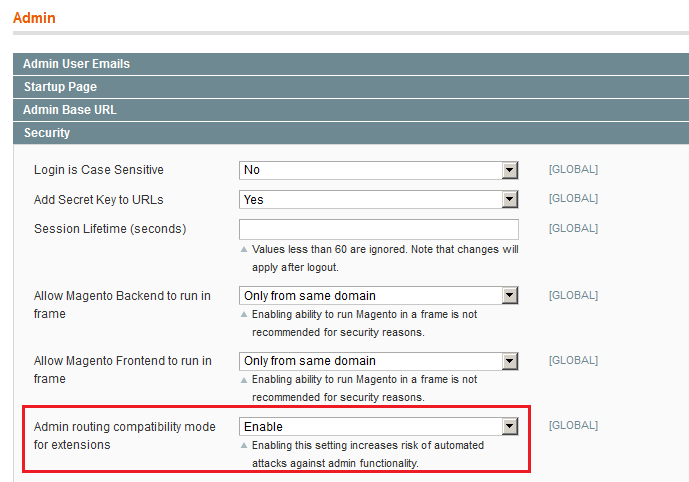
1) Did you disable the following setting
System >Configuration >Advanced >Admin >Security >Admin routing compatibility mode for extensions
By default it is set to enable, it must be disabled. When it is enable it provides the backward compatibility with admin routing.
Once this setting is disabled your Helios Vimeo Video Gallery admin Manage video gallery link will not work.(Check SUPEE-6788 documentation)
Ransom ware may be injected using the by taking advantage of security loopholes of hosting environment also.
If you just started the development you can try to rework on it or use a backup.
Before doing all these take advice from some security expert to identify the root cause of the attack.Also inform your hosting provider.
Next time follow these instructions also.
1) Check the Magento files and folders permissions once and set those to recommended one.
2) Stop using FTP, use SFTP instead.
3) Do not use Magento default admin url.Use a custom url for the admin panel access.
4) Change all the user names and passwords for the cPanel,FTP (better do not use it).
5) If you worked with some third party for development work on your Magento installation then change all user name and passwords.
Also change all the admin access granted to them. Any users created for SOAP and REST api access.
6) Add IP restriction to your Magento admin so that it can be accesses from a particular ip address only.(First acquire a static ip address)
7) Restrict your files under following location from being visible publicly by accessing in browser url.
a) var/log
b) app/etc
8) Also visit https://magento.com/security check the best practices section there.
9) Use a good Antivirus on your system also.
10)Do not use magento admin password for any other accounts.
Also visit following:
1) https://community.magento.com/t5/Security-Patches/Hacked/m-p/30037#M1476
2) https://magento.com/security/best-practices/security-best-practices
Note : I am not a security expert above mentioned are best practices.(Consult a security expert )
Problem Solved Click Accept as Solution!:Magento Community India Forum
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Ransom Ware on Clean install of 1.9.2.4
Is there anything more that you can share? Do you access the server via FPT? Did you have good passwords?is there anything in the logs (including auth log, showing ssh sessions)? Did it encrypt only Magento files or whole filesystem?
Would you be able to share error and access logs from apache to security@magento.com?