- Forums
- :
- Core Technology - Magento 2
- :
- Magento 2.x Technical Issues
- :
- Re: Code in place of customer name - Is this an at...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
Code in place of customer name - Is this an attack?
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Code in place of customer name - Is this an attack?
So even upgrading to Magento 2.4.4 hasn't solved this issue.
Anyone Forum Moderator, please jump it.
Anyone else experienced this?
Shouldn't there me form validation as standard?
Thanks
Andy
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Code in place of customer name - Is this an attack?
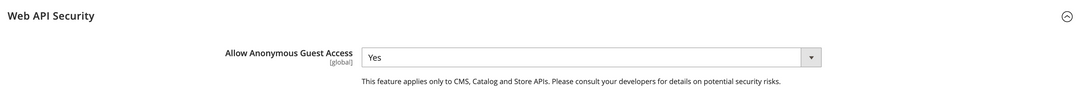
If you are seeing orders being created, perhaps check to see if you are allowing guest access to the API:
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Code in place of customer name - Is this an attack?
1) You can add 'getTemplateFilter' to the list of banned keywords. You can also add citytoohot.fr.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Code in place of customer name - Is this an attack?
Hi,
We are having the same issue on 2.4.4-p2. We are fully up to date and patched.
I believe this is a exploit linked to the email template vulnerability in previous releases yet we have received an order with getTemplate code as the name despite characters being limited to alphanumeric only and guest API is disabled.
@ianleaphotfa91 how do you add banned keywords described?
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Code in place of customer name - Is this an attack?
Same issue on 2.4.5-p1.
Guest WEB API access is disabled.
Guest checkout is disabled.
How do they create orders?
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Code in place of customer name - Is this an attack?
There doesn't seem to be much from Magento regarding this issue.
If you're patched & up to date then this exploit will be unsuccessful. It attempts to inject using the email template vulnerability identified by Magento in February 2022.
Related Patches: MDVA-43395 & MDVA-43443. See Patch release notes.
There is a Github issue open regarding access via the API when the Guest API & Guest Orders are disabled. Seems that Magento are working on this.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Code in place of customer name - Is this an attack?
Did you get an answer to your banned keyword query? I don't know how to do it either ![]()
Many thanks
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Code in place of customer name - Is this an attack?
Same is there in Magento 2.4.5 P5.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Code in place of customer name - Is this an attack?
Ok, I managed to deal with this, creating a custom module and block order execution if firstname or lastname contain characters like Curly Bracket, Less-Than Sign. etc. and log the attempt too. Hope this help.
https://github.com/magento/magento2/issues/39002#issuecomment-2291143582
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Code in place of customer name - Is this an attack?
Ok, I managed to deal with this, creating a custom module and block order execution if firstname or lastname contain characters like "}","{", <.. etc. and log the attempt too. Validation also for: Customer creation, Customer fields update. Hope this help.
- « Previous
-
- 1
- 2
- Next »