- Forums
- :
- Core Technology - Magento 1.x
- :
- Magento 1.x Security Patches
- :
- Pepe frog image magento 1 attack - mystery surroun...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
Pepe frog image magento 1 attack - mystery surrounding how code is executed
SOLVED- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
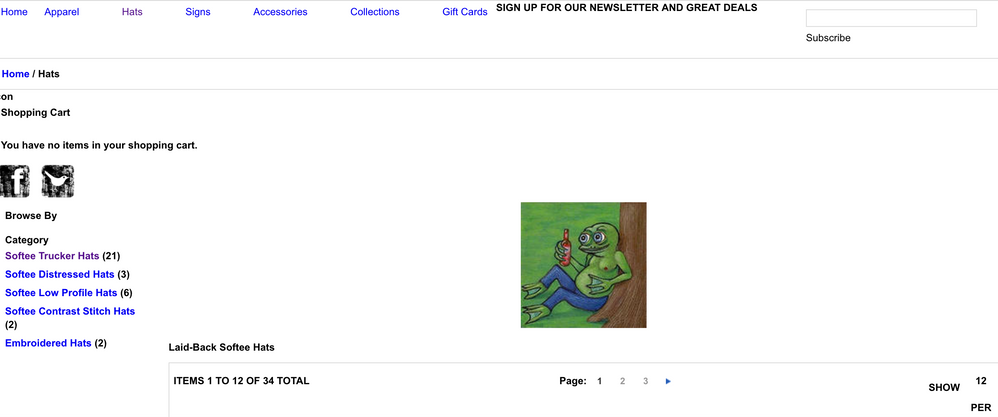
Hi, I have been investigating an attack on a site that happened around the end of 2016. In the attack a jpeg image was uploaded with PHP code appended. This is the image (with code removed).
Unfortunately we do not have logs from the period when the attack happened. I can well believe that the admin passwords may have been brute forced or we weren't quick enough applying SUPEE-8788
Doing a google image search I see plenty of other examples of magento 1 stores attacked with similar images. The names of the images vary but they are always uploaded to the media/catalog/category directory of the attacked store. The code at the end of these images also differs in purpose. Some just dropping a web shell, or simple backdoor but also sometimes installing the Visbot malware.
The puzzling part is how these images are used to gain PHP execution of the appended code. In particular the first line of the code does this.
$p = str_replace('index.php','',$_SERVER['SCRIPT_FILENAME']);
with $p then being used as the base path for writing the attack files.
This would seem to indicate that the code is executed through
public/index.php
The only construct I can think of that would excute a jpeg as PHP code through /index.php is something like:
require 'media/catalog/category/imagefile.jpg';
But have no idea how that could occur.
One interesting thing to note is that in the wild the images are sometimes used as category headers as they would be if uploaded through the category admin e.g.
Does anyone else have any experience of these attacks? Or do you have any clue how the code execution works? AFAIK MagPleasure's File System module was not installed which seems to be a common route to web shell from admin access.
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have managed to work out a probable way of how this was done. But cannot say more at this time.
In the meantime if anyone has been affected by this I would recommend the following post on how to examine your site http://gwillem.gitlab.io/2017/04/12/magento-breach-analysis/.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Pepe frog image magento 1 attack - mystery surrounding how code is executed
We experienced this. Our scenario turned out to be a credit card skimmer. Someone got in and installed a browser based SQL app then installed the skimmer. Check these files:
htaccess.php
OnepageController.php
phpinfo.php
progressreview.js
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have managed to work out a probable way of how this was done. But cannot say more at this time.
In the meantime if anyone has been affected by this I would recommend the following post on how to examine your site http://gwillem.gitlab.io/2017/04/12/magento-breach-analysis/.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Pepe frog image magento 1 attack - mystery surrounding how code is executed
The full story here https://securingmage.com/2017/06/13/the-strange-tale-of-the-frog-images/